Passkeys for Businesses: Benefits, Challenges, and How to Start
The password era is ending, and that helps SMBs
Google made passkeys the default sign-in option for personal accounts and reports massive usage growth. Across ecosystems, more than 15 billion accounts can now leverage passkeys, and adoption is accelerating as consumer and business credential managers add support. (Passwordless by default)
Third-party snapshots echo the momentum. Dashlane reported a four-times increase in passkey usage among its users in 2024, with materially higher successful login rates compared to passwords. The trend is moving from novelty to routine.

Why passkeys are safer and easier
Passkeys use public-key cryptography bound to the legitimate website or app. There is no shared secret to steal, reuse, or phish, and users sign in with a device unlock like Face ID, Touch ID, or a PIN. This design closes two of the biggest failure modes in SMB breaches: password reuse and phishing.
Microsoft and Apple have enterprise pathways that let organizations roll out phishing-resistant, password less methods at scale. Entra ID now includes policy controls to require passkey-class methods, and Apple supports managed passkeys synced with iCloud Keychain for Managed Apple Accounts. (Microsoft Learn)

What could trip you up
Device and platform mix
Older hardware or browsers may not support authenticators fully. Inventory your fleet and plan upgrades where needed.
Account recovery
You still need secure recovery processes for lost devices. Enterprise guides from Microsoft and Apple outline bootstrapping and recovery patterns for passwordless deployments.
Federation and SaaS readiness
Not every SaaS app exposes passkeys yet, though coverage grows monthly. Use identity provider features to enforce phishing-resistant MFA where passkeys are not supported, then enable passkeys as apps catch up.
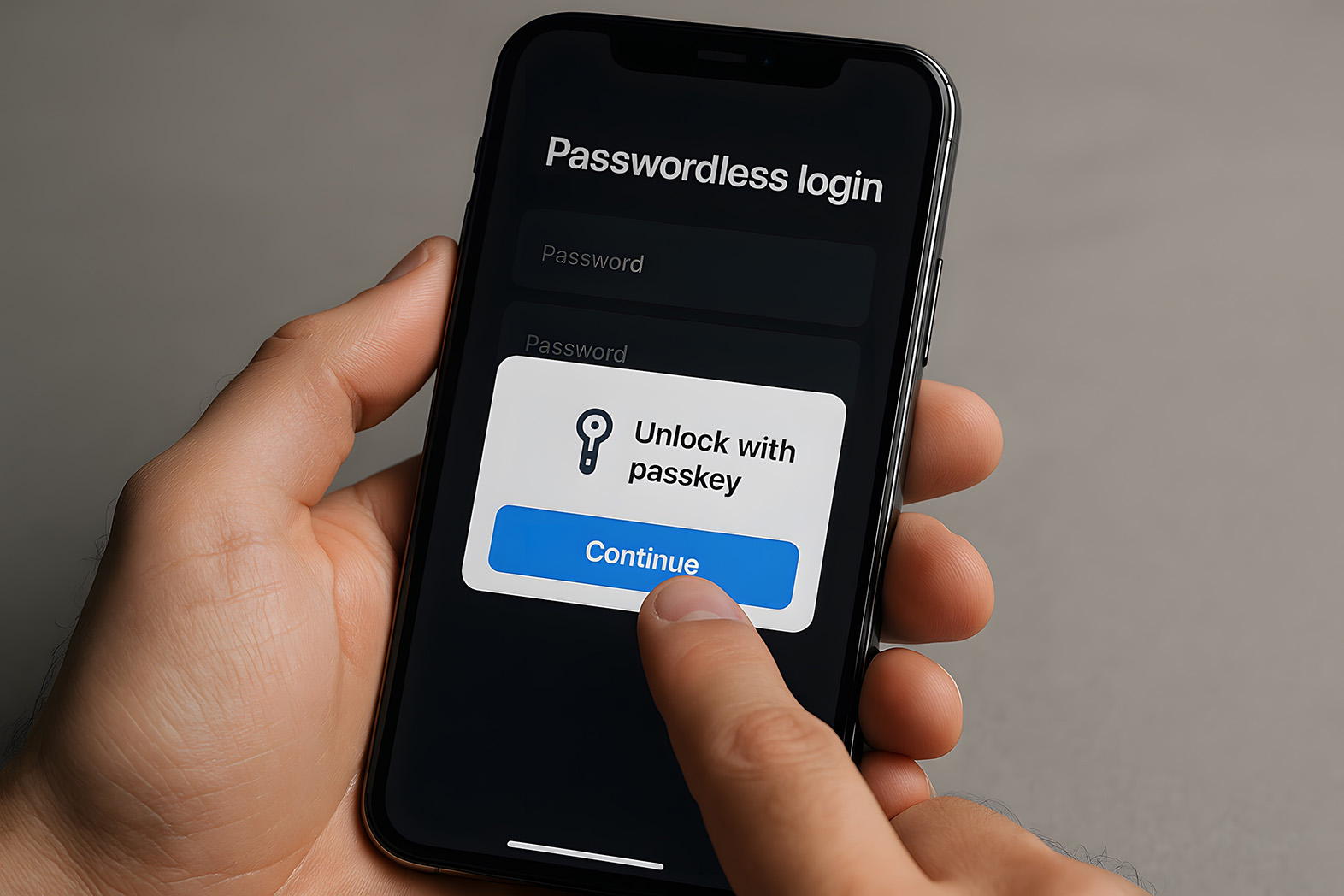
A pragmatic SMB rollout plan that avoids trial and error
1. Align to business risk
Start with a short readiness review. Identify the roles and apps that create the most exposure and the most friction. Prioritize phishing resistant sign-in for those first so you cut real risk early.
2. Prove it with a focused pilot
Run a time-boxed pilot with a small champion group across departments. Measure login success, support tickets, and user sentiment. Use those insights to shape the broader rollout and training.
3. Protect high-impact identities
Move executives, finance, IT admins, and anyone who moves money to passwordless first. Pair passkeys with stronger factors where needed so sensitive workflows stay fast and secure.
4. Roll out in waves, not all at once
Expand by department and application tier. Make passkeys the preferred experience as coverage grows, then turn down weaker factors only when adoption data says users are ready.
5. Make it stick
Give people simple “what changes for me” guidance, not a textbook. Track password reset volume, recovery requests, and phishing outcomes so leaders see the value and teams build confidence.
Why bring in ThinkSwift
The outcome
Faster sign-ins, fewer phishing paths, less reset pain. Your team gets a modern login experience. You get measurable risk reduction without the guesswork.
Recent Blogs
Marketing says traffic is up. Ads are getting clicks. Campaigns report “good engagement”. Sales says the pipeline still feels light. If that sounds familiar, your…
Read MoreA CFO types “IT support for manufacturers Toronto” into Google. At the top of the page, they see two competitors. One is running a paid…
Read MoreMost attribution debates pretend to be about science. They’re about credibility. Sales wants proof that marketing’s dollars create pipeline. Marketing wants recognition that discovery takes…
Read MoreMarketing says traffic is up. Ads are getting clicks. Campaigns report “good engagement”. Sales says the pipeline still feels light. If that sounds familiar, your…
Read MoreA CFO types “IT support for manufacturers Toronto” into Google. At the top of the page, they see two competitors. One is running a paid…
Read MoreMost attribution debates pretend to be about science. They’re about credibility. Sales wants proof that marketing’s dollars create pipeline. Marketing wants recognition that discovery takes…
Read More


